Blackshades Net Can Best Be Described as a Wrapper
Which layer is responsible for determining the best path a packet should travel across an internetwork. This malware was recorded in the wild for the first time in 2013.

The Color Thesaurus Shades Of Black Writing Color Names
Baleage allows harvesting high-moisture hay with minimal harvest loss.

. Sets found in the same folder. DDoS Tool RAT Question 80 0 1 point Buffer overflow attacks allow an attacker to modify the _____ in order to control the process execution. Each of these monikers has been used to describe any member of the internet subculture whose primary interest is to test the security limits of computer systems be their motivations malicious or otherwise.
Wireshark can be used in a variety of ways however the most common configuration for Wireshark and the configuration that you ran in the lab has the software running. Nearly every digital camera today offers a black-and-white option. And to get the best picture possible it pays to follow them.
Turn on the Windows Firewal. Question 73 1 point With Cross Site Scripting attackers can inject malicious ____. The Human Experience refers to those events that all of us in life can relate to regardless of the time period or the society in which we were born.
In a peer-to-peer configuration. Biology questions and answers. That gives you a number of ways to work with a picture during conversion.
In the simplest terms Wireshark is used to capture all. IPS IDS low interaction. On a local area network.
But you can get far more interesting pictures if you wait and convert them to black and white on your computer. Which statement does not describe a method whites used to keep blacks from exercising their rights. Bot Wrapper DDoS Tool RAT Question 73 1 point With Cross Site Scripting attackers can inject malicious ____.
Connect and share knowledge within a single location that is structured and easy to search. It can be a strong cultural statement a fashionable accessory or a smart fix for those days when you dont want to style your hair. Background Scenario.
It was well publicized that BlackShades Net was used as an attack tool against. رابط تحميل البرنامج مجاني كلمة شكر تكفي. The Internet Hate Machine.
Which of the visual elements can best be described as the path of a moving point. What is a typical investment range for. Capital from a large audience usually through the internet.
Crowdfunding can best be described as. JavaScript HTML VBScript Flash Question 74 1 point. Question 78 0 1 point BlackShades Net can best be described as a.
In reference to crowdfunding a backer is best described as. Choose all that apply Question 73 options. Maltrail is a malicious traffic detection system utilizing publicly available blacklists containing malicious andor generally suspicious trails along with static trails compiled from various AV reports and custom user defined lists where trail can be anything from domain name eg.
On a local host. 1 Adwind Rat v30 Cracked 2 BlackShades Fusion Source Code 3 DenDroid Source Code 4 Hunter Exploit Kit. BlackShades Net can best be described as a.
OwnFone users can now create a phone with Braille buttons. The two types of honeypots include. View the answer now.
By Bryant Kuehner Hackers on steroids. - motion - time - mass - line - light. Depending on plastic wrap quality and wrapping techniques you can expect 15 to 25 of bales to have some degree of spoilage says Jamie Patton University of Wisconsin County Extension agent.
Question 72 1 point BlackShades Net can best be described as a. Starting at 100 60 British pounds according to the BBC. Available in many colors and patterns fabrics and sizes headwraps are usually about 60-72.
RAT Bot Wrapper DDoS Tool. An African Headwrap or African Head Wrap two words is a piece of cloth tied around the head in an intricate style. TrueFalse Third-party cookies can be stolen and used to impersonate the user while first-party cookies can be used to track the browsing or buying habits of a user.
Logic holds that black plastic should absorb more heat and speed fermentation he adds. Access control One job that a router performs is that of gatekeeper which means that it can be configured to only allow certain packets access into the network based on a. Bot Wrapper DDoS Tool RAT.
Blackshades has the ability to infect and hack multiple computers from the release of a bait that the hacker can make use of an improved version of blackshades was released shortly after the original release of the primary version when hacking organizations like Octagonun and Cyber-Sec decided to develop special features for coupling to the. The movement of molecules with their concentration gradient from areas of higher concentration to areas of lower concentration. Explicit session ID Cloned session Hash BlackShades Net can best be described as a.
From a probe or hub. High interaction According to your text most of the webservers run which of the following. Choose all that apply Question 73.
UK-based OwnFone a company that lets users design their own mobile devices introduced what its calling the worlds first Braille phone. BlackShades Net can best be described as a. Mashable - 20 May 2014 0232.
Part 15 Active transport can best be described as Multiple Choice the diffusion of water from areas where water concentration is higher to areas where water concentration is lower. Was asked on May 31 2017. Predators both piscatorial and of the feathered variety are aware of this migration with the entire scheme of things coming together in what can only be described as a feeding frenzy.
Governments businesses and individual users are increasingly the targets of cyberattacks and cybersecurity incidents are becoming more common. In 2016 it was estimated that businesses lost 400 million dollars annually to cyber criminals. Raw download clone embed print report.
Spring is not a good time to be a young shad on the Mississippi River. In this lab you will create three hypothetical cyber attackers each with an. Net worth over 1 million or income over 200K.
Young-of-year shad are now about 2-3 inches long and programmed to swim en masse upstream.

3m Black Shade Window Tinting Foil Good Car Tinting Foil
Usage Markdown Index Md At Main Imagemagick Usage Markdown Github

Set Of Vehicle Cartoon Stock Vector 112322129 Shutterstock Cartoon Excavator Fishing Net
Blackshades Trojan Users Had It Coming Krebs On Security
Blackshades Trojan Users Had It Coming Krebs On Security
![]()
Carbon Fiber Background In Black Shades Stock Photo Crushpixel
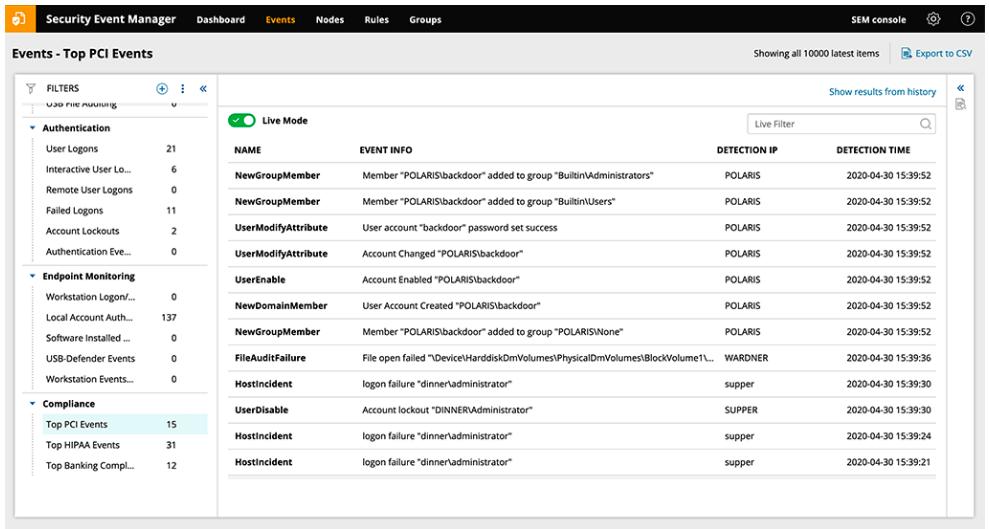
11 Best Rat Software Detection Tools For 2022 Free Paid

Blackshades Trojan Users Had It Coming Krebs On Security

Nighttime Storm Eyeshadow Kit Makeover Essentials Eyeshadow Black Eye Pencil

Blackshades Trojan Users Had It Coming Krebs On Security
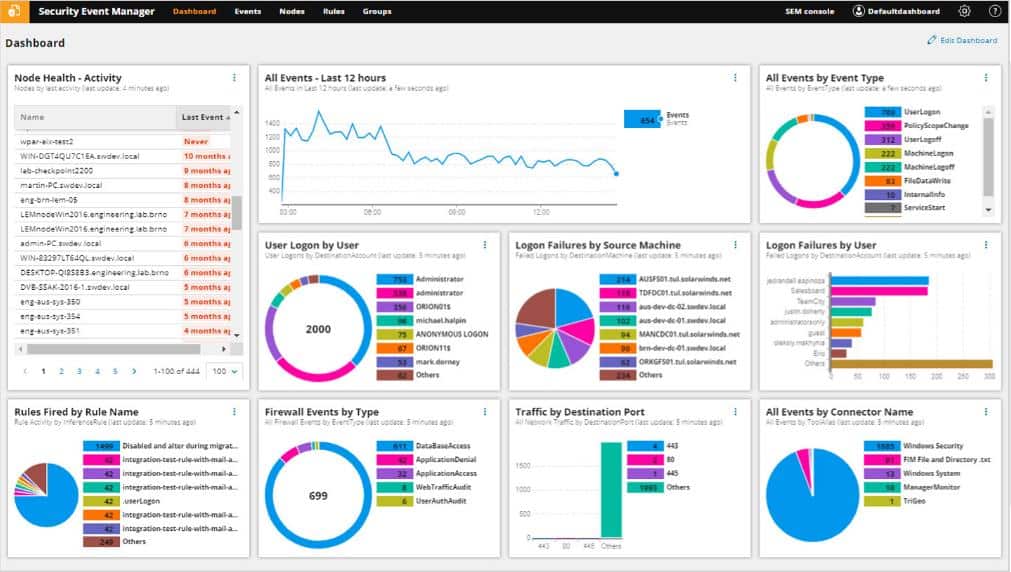
11 Best Rat Software Detection Tools For 2022 Free Paid
Re Onenote For Windows 10 White Colour Is Now Light Gray Duplicates Pen Upon Changing Microsoft Tech Community
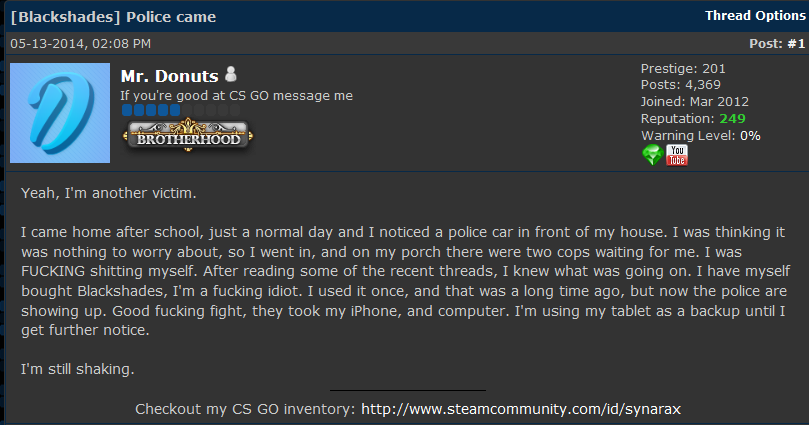
Blackshades Trojan Users Had It Coming Krebs On Security

Re Onenote For Windows 10 White Colour Is Now Light Gray Duplicates Pen Upon Changing Microsoft Tech Community

Calameo Narrative Of A Voyage To Madeira Teneriffe And Along The Shores Of The Mediterranean




Comments
Post a Comment